Owasp Top 10 Android
OWASP Top 10. Here were sharing top 10 Vulnerable Apps for Android platform through which you can easily practice and enhance your skills.

Owasp Mobile Top 10 Security Vulnerabilities And Attack Prevention Cyphere Securing Your Cyber Sphere
Appknox Vulnerable Application PIVVA by High-Tech Bridge Android InsecureBankv2 DVHMA Damm Vulnerable Hybrid Mobile App DIVA Android OWASP Security Shepherd OWASP-mstg Vulnerable Android App Oracle Dodo Vulnerable Bank.
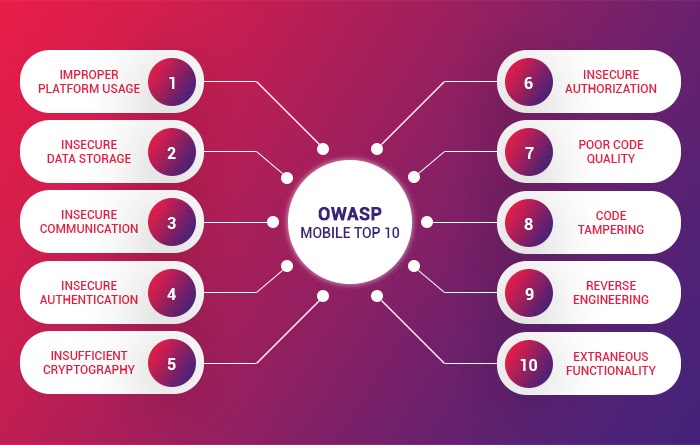
. M1 Improper Platform. Static analysis approaches have been proposed for various assignments including. OWASP Mobile Top 10 2016.
To start an Activity coordinating with other programs like browsing a web page. Through the project our goal is to classify mobile security risks and provide developmental controls to reduce their impact or likelihood of. OWASP Mobile Top 10 Remediation Measures for This Vulnerability.
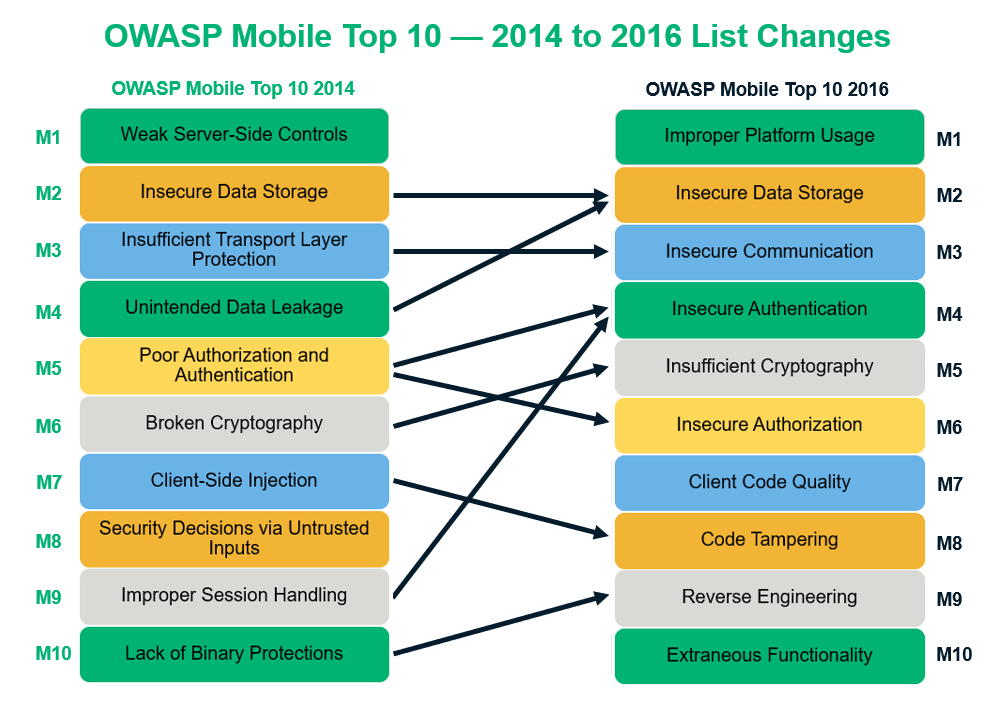
In 2013 OWASP polled the industry for new vulnerability statistics in the field of mobile applications. As broadcasts to inform interested programs of changes or events. Below is the OWASP Mobile Security Top 10 vulnerabilities.
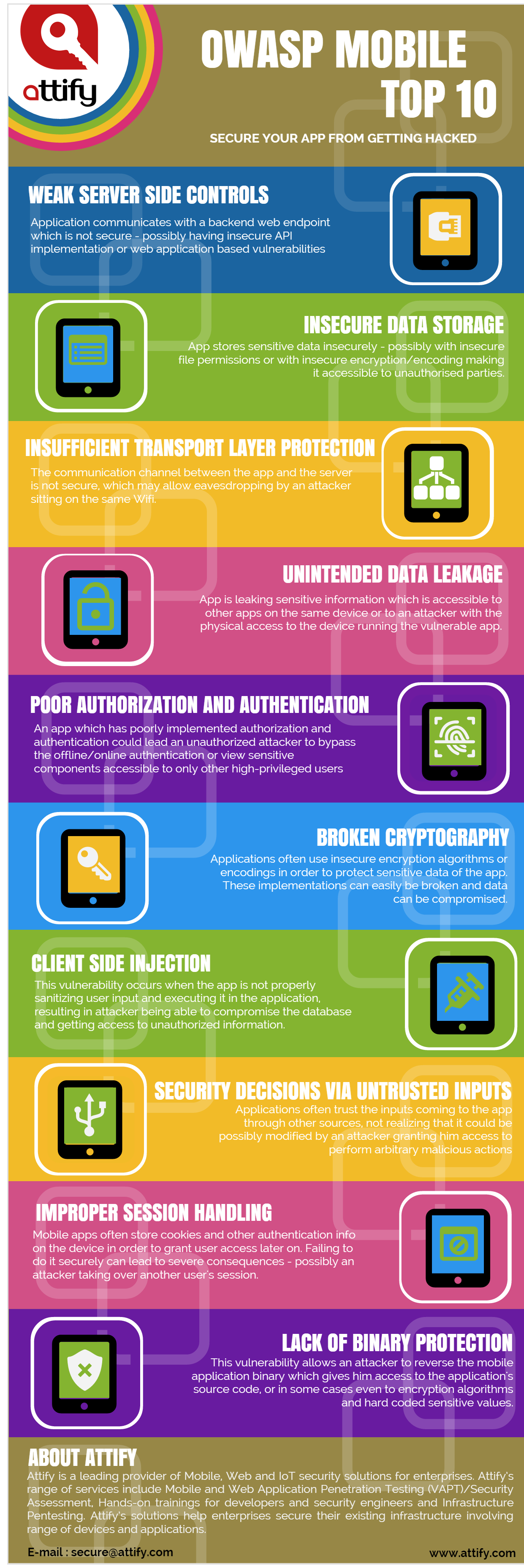
M2 Insecure Data Storage. Intents are used in a number of ways on the Android platform. OWASP Top 10 2021 - RELEASED.
OWASP Mobile Security Top 10 For Android And iOS apps Published on December 4 2015 December 4 2015 53 Likes 9 Comments. Every year OWASP releases reports on the top 10 most critical web and mobile application security risks powerful awareness documents for application security that represent a broad consensus about the most critical security risks to apps. OWASP IoT Top 10 Series.
Poor Authorization and Authentication. Android intents used to request an action from another app component that are marked public may reveal sensitive information or permit unauthorized execution. Our mobile application testing is based on the OWASP Mobile Security Testing guide and checklist to ensure that the requirements of a secure and robust application are met.
What are the OWASP mobile top 10 risks. Among the 30 applications 17 were vulnerable to MITM. This is the second article in our OWASP Mobile Top 10 series which aims to flesh-out the OWASP recommendations with some concrete examples that you can apply to your iOS and Android applications today.
Security feedback during code review is your opportunity to learn feel more engaged. Implementation of the OWASP Mobile TOP 10 methodology for testing Android applications. Ad Manage Website Application Security with Indusface WAS Cloud-Based OWASP Top 10.
According to BetaNews among the 30 best applications with more than 500000 downloads 94 contain at least 3 average risk vulnerabilities while 77 contain at minimum two high-level vulnerabilities. Lets look at the Top 10 OWASP mobile security vulnerabilities. Security Decisions Via Untrusted Inputs.
The OWASP Mobile Security Project is a centralized resource intended to give developers and security teams the resources they need to build and maintain secure mobile applications. OWASP Mobile Top 10. The following risks were finalized in 2014 as the top 10 dangerous risks as per the result of the poll data and the mobile application threat landscape.
KONTRA OWASP Top 10 is our first step in that direction. OWASP Top 10 2017 - SUPERCEDED. Static Analysis of Android Application Tools Used.
Internet usage via mobile has surpassed fixed Internet access. And today we will explore the oldest and most common mistake which is a weak password. If you havent already please check out our OWASP Mobile Top 10 2016.
Weak Server Side Controls. At KONTRA we believe every software engineer should have free access to developer security training. Check your Website Security Issues with Indusfaces Free Website Security Scan.
Weak or Hardcoded Password Policy OWASP. Inspired by real-world vulnerabilities and case studies we have created a series of interactive application security training modules to help developers understand identify and mitigate security vulnerabilities in. This OWASP mobile security risk is something that you must address on the server side of things.
Weak Server Side Controls. 41 out of 5 41 147 ratings. Static analysis is the exploitation of strategies that parse the program source code or bytecode regularly navigating program routes to check the program properties.
We have released the OWASP Top 10 - 2017 Final OWASP Top 10 2017 PPTX OWASP Top 10 2017 PDF OWASP Top 10 Leadership. Everyday popular mobile apps on the Google Play and App Store are found to be vulnerable to the OWASP Mobile Top 10 making it harder to protect consumers from the risks. Using Context s startActivity method.
Up to 10 cash back The OWASP top 10 demystified A practical guide for ethical hackers developers and software testers to the 10 most prevalent security defects of 2017 Rating. Please log any feedback comments or log issues here. M1 Android Intents.
In the last blog we had explored OWASP IoT Top 10 vulnerabilities overview now we will explore the impact of each of these OWASP vulnerabilities on IoT technologies and product development. Official OWASP Top 10 Document Repository. Ad Your code is more secure with SonarQube to automatically detect OWASP vulnerabilities.
There are currently four co-leaders for the OWASP Top 10. Published by Shubham Ingle at May 4 2021. Insufficient Transport Layer Protection.
The OWASP community believes that adopting the OWASP Top 10 is perhaps the most effective first step towards changing.

Owasp Mobile Top 10 Comprehensive Guide To Counter Mobile App Risks
Owasp Mobile Security Top 10 For Android And Ios Apps
Owasp Mobile Top 10 Vulnerabilities Mitigation Strategies Infosec Insights
Comments
Post a Comment